Top 8 Vulnerability Management Tools
Explore the best VRM software to streamline due diligence, monitor vendors in real time, and support compliance, reporting, and business continuity.
Published on November 05, 2025
Last updated on January 07, 2026
Third-party relationships can drive efficiency and innovation but can also expose organisations to significant risks. Vendor Risk Management (VRM) software provides the tools and automation necessary to identify, assess, and monitor vendor-related risks—from cybersecurity threats to compliance breaches.
In a landscape where supply chain dependencies are increasingly complex, understanding and managing third-party risk has become an essential function for governance, compliance, and business continuity. The right VRM software not only centralises vendor data but also automates risk assessments, reporting, and monitoring, allowing teams to focus on strategic initiatives rather than manual tracking.
In this article, we will explore what Vendor Risk Management software is, its key features, and the top platforms to consider in 2026.
Vendor Risk Management (VRM) software helps organisations evaluate and monitor the risks posed by third-party vendors, suppliers, and service providers. These tools enable teams to manage vendor onboarding, risk assessment, due diligence, contract tracking, and ongoing performance monitoring.
A strong VRM system consolidates information from multiple sources to provide a clear picture of vendor performance and compliance posture. It assists in identifying potential risks before they materialise—such as data breaches, operational failures, or non-compliance with industry standards.
Ultimately, VRM software helps organisations maintain oversight and accountability across the entire vendor lifecycle, reducing exposure to risk and supporting regulatory compliance.
Selecting the right VRM platform requires understanding which features are essential for effectively managing third-party risk.
Automated assessments streamline the process of collecting and analysing vendor data. Questionnaires, risk scoring, and follow-up workflows can be automated to save time and ensure consistency.
Continuous monitoring provides real-time insights into a vendor’s security and compliance status. It helps detect emerging threats or incidents that may affect business operations.
A single repository for all vendor data, including contacts, contracts, compliance documents, and assessments, simplifies management and enhances visibility across departments.
Dynamic risk scoring tools evaluate vendor performance based on pre-defined criteria and real-world data. Dashboards and analytics support data-driven decision-making and quick identification of high-risk vendors.
Integration with other systems, such as procurement, GRC, and ITSM tools, ensures a seamless exchange of information and a holistic view of vendor risk across the organisation.
Comprehensive reporting and audit trails provide evidence for regulatory compliance and internal audits, improving transparency and accountability.
Continuity2’s VRM module within the Meridian platform offers an industry-leading approach to managing vendor risk across the entire lifecycle. Its intelligent automation and analytics capabilities help organisations streamline onboarding, risk assessment, and monitoring processes within a unified resilience framework.
Key Features:
Best for: Enterprises seeking a fully integrated resilience and risk management system combining vendor risk, business continuity, and operational resilience within a single platform.
OneTrust’s Third-Party Risk Management platform automates vendor onboarding and risk evaluation while aligning with global regulatory standards such as GDPR, ISO 27001, and SOC 2.
Key Features:
Best for: Organisations prioritising regulatory compliance and data privacy in third-party relationships.
ProcessUnity offers a comprehensive vendor risk management solution designed for centralised oversight and automation. It provides full visibility into vendor relationships and their associated risks.
Key Features:
Best for: Mid-to-large organisations needing detailed oversight of vendor risk and compliance workflows.
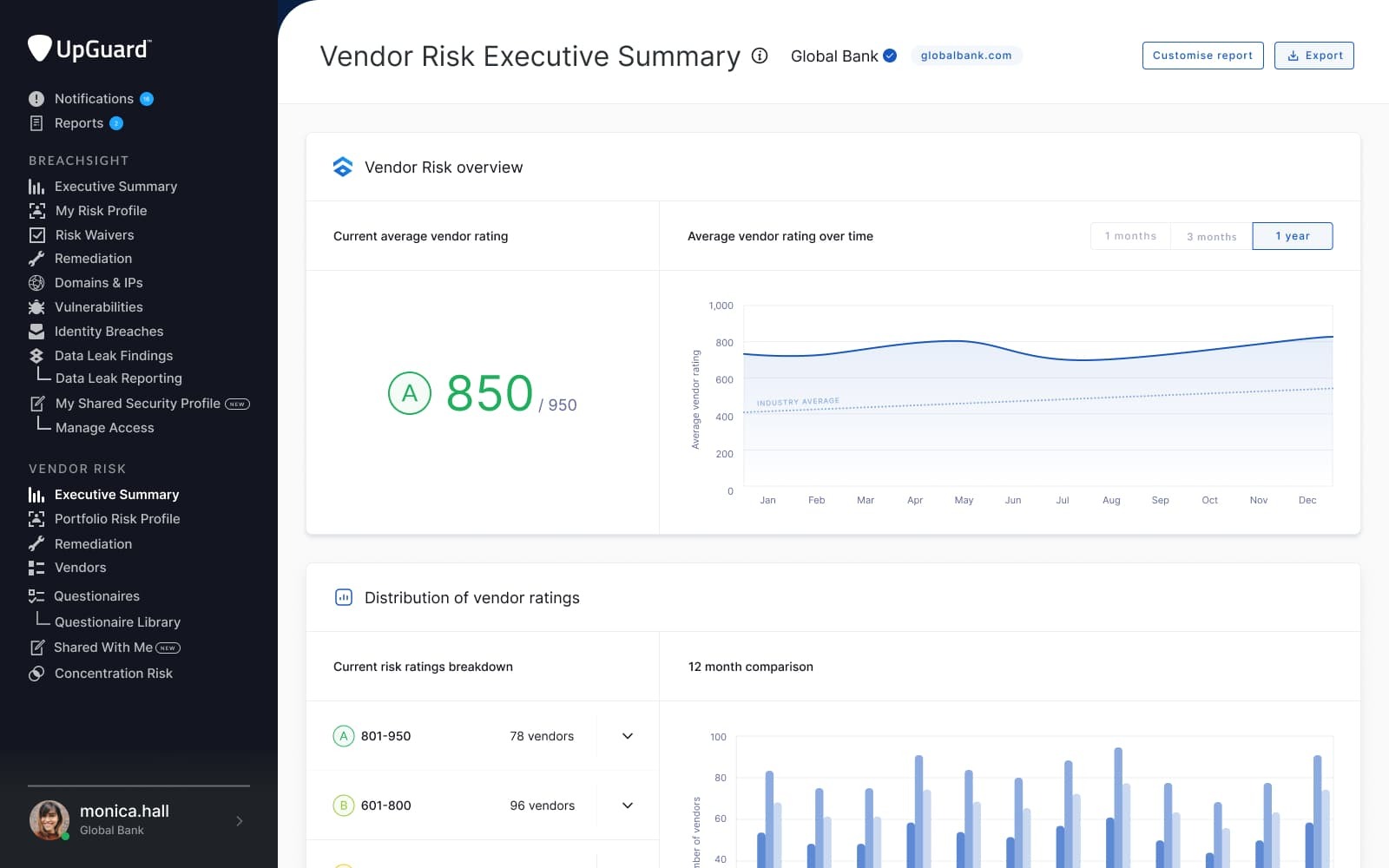
UpGuard combines VRM with cybersecurity ratings to deliver continuous visibility into vendor security posture.
Key Features:
Best for: Security-conscious organisations focusing on cyber risk monitoring.
Venminder specialises in vendor lifecycle management, offering tools for onboarding, monitoring, and reporting with a strong compliance orientation.
Key Features:
Best for: Financial institutions and regulated industries requiring strict due diligence processes.
SecurityScorecard delivers cyber risk ratings and insights for managing third-party security. It continuously evaluates vendors using external data sources.
Key Features:
Best for: Businesses seeking continuous cyber risk intelligence across their supply chain.
Prevalent offers a mature third-party risk management platform with automated assessments and vendor intelligence.
Key Features:
Best for: Organisations seeking a scalable VRM solution with extensive assessment libraries.
Vendor management software empowers organisations to proactively identify, assess, and mitigate third-party risks while improving efficiency, compliance, and resilience.
A centralised platform provides a single view of all vendor-related risks, enabling better prioritisation and mitigation efforts.
VRM software ensures documentation and audit readiness for various compliance frameworks, reducing the risk of penalties.
Automated workflows eliminate manual processes and accelerate vendor onboarding, monitoring, and reporting.
With real-time analytics and dashboards, organisations can make informed decisions based on risk trends and performance indicators.
Monitoring vendor resilience helps ensure critical services remain available, even when external partners face disruptions.
Vendor risk management is no longer a back-office compliance function—it’s a strategic pillar of operational resilience. Organisations that integrate vendor risk insights into their continuity and resilience frameworks can better anticipate disruptions, safeguard compliance, and maintain business stability even under pressure.
Book a Demo with Continuity2 to see how our Meridian platform helps you automate vendor oversight, strengthen supply chain resilience, and enhance enterprise-wide continuity planning.
Founder & CEO at Continuity2
With over 30 years of experience as a Business Continuity and Resilience Practitioner, Richard knows the discipline like the back of his hand, and even helped standardise BS25999 and ISO 22301. Richard also specialises in the lean implementation of Business Continuity, IT Service Continuity and Security Management Systems for over 70 organisations worldwide.


Founder & CEO at Continuity2
With over 30 years of experience as a Business Continuity and Resilience Practitioner, Richard knows the discipline like the back of his hand, and even helped standardise BS25999 and ISO 22301. Richard also specialises in the lean implementation of Business Continuity, IT Service Continuity and Security Management Systems for over 70 organisations worldwide.
Explore the best VRM software to streamline due diligence, monitor vendors in real time, and support compliance, reporting, and business continuity.
Discover the top 10 Threat Intelligence Platforms of 2026 to detect, analyse, and respond to cyber threats with greater speed and precision.
Explore the best third-party risk management software to automate vendor assessments, track compliance, and reduce exposure across your supply base.
Discover the top 7 Supply Chain Risk Management (SCRM) tools of 2026 to monitor suppliers, predict disruptions, and build supply chain resilience.
Find the best supply chain management software of 2026 and gain real-time visibility, streamline planning and logistics, and protect business continuity.
Compare the top supplier monitoring tools of 2026 and find the right software to enhance supplier visibility and protect your supply chain.
Find the best SIEM tools to detect threats faster, automate incident response, ensure compliance, and strengthen your organisation’s cyber resilience.
Choose the right risk analysis software to automate assessments, gain real-time insights, meet compliance, and strengthen resilience—see our top 7.
Discover top risk and resilience software for manufacturing in 2026—SOAR automation, visibility, and compliance to protect uptime and supply chains.