Jump to a section
As organisations and individuals rely more heavily on online platforms for their day-to-day operations, the significance of cyber security cannot be overstated.
This article provides a comprehensive overview of the latest cybersecurity statistics for 2026, drawing from credible sources such as the UK Home Office, IBM, World Economic Forum, and many others.
We delve deep into the numbers, offering valuable insights into the current state of cybersecurity across four overarching areas:
As we navigate these cybersecurity statistics, you will witness the magnitude of the challenges faced and the efforts being made to secure our digital future.
Statistics of Economic Impact of Cyber Attacks
The economic repercussions of cyber attacks are profound and extensive, affecting businesses of all sizes and sectors. The financial strain is not only in immediate costs incurred post-breach, but also in the long-term strategies and investments made to counteract such threats. The following statistics shed light on this financial dimension of cyber security.
- Just over four in ten UK businesses (43%) and three in ten charities (30%) report having experienced a cybersecurity breach or attack in the past year, equating to 612,000 businesses and 61,000 charities. (GOV.UK)
- Across UK businesses, 29% of businesses overall and 48% of small businesses conduct risk assessments covering cybersecurity. (GOV.UK)

- The average cost of the most disruptive cyber breach was £3,550 for businesses and £8,690 for charities (excluding those who reported their most disruptive breach costs as £0). (GOV.UK)
- Cloud and connected product attacks are the top 2 cyber threats organisations are least prepared to address. (PwC)
- The global average cost of a data breach in 2025 was USD 4.44 million. (IBM)
- In 2024, the median ransom payment following a ransomware attack was approximately USD 200,000, with most attacks receiving little to no public attention. (Check Point)
Statistics of Business Preparedness and Strategic Response
How prepared are businesses to face the burgeoning cyber threats? The readiness of an organisation to counteract cyber threats is a reflection of its strategic foresight and its emphasis on cyber security. These statistics provide insights into the strategic positioning of businesses vis-à-vis cyber threats.
- Cybersecurity has remained a high priority for 72% of businesses and 68% of charities across the previous 12 months. (GOV.UK)
- Cybersecurity is a higher priority for finance or insurance (97%), utilities or production (89%), professional, scientific or technical (85%), or administration or real estate (83%) than other sectors. (GOV.UK)
- 42% of businesses overall and 37% of charities have sought external guidance across the past year. (GOV.UK)
- Staff training and awareness raising activities on cyber risks and security are more prevalent in large UK businesses (at 76% compared to 19% of businesses overall). (GOV.UK)
- Additional staff training or communications are the most common preventative measure adopted after a security breach, in 32% of businesses and 38% of charities.(GOV.UK)
- 70% of large businesses, 57% of medium businesses, and 39% of high-income charities have a formal cybersecurity strategy in place. (GOV.UK)
- 60% of business and tech leaders rank cyber risk investment as one of their top strategic responses due to ongoing geopolitical uncertainty. (PwC)
- 63% of organisations currently lack both cybersecurity strategy and capability, making them prime targets for cyber threats. (Accenture)

- Only 6% of businesses feel confident of withstanding cyber attacks targeting specific vulnerabilities, with roughly half only feeling "somewhat capable". (PwC)

- 48% of organisations that have experienced a major attack are prioritising managed services to address cyber talent gaps. (PwC)
- 34% of organisations have a mature cyber strategy but only 13% possess the advanced cyber capabilities needed to defend against modern AI threats. (Accenture)
- One in three CEOs cite cyber espionage and loss of sensitive information or intellectual property (IP) theft as a top concern. (World Economic Forum)
- 50% of organisations rank information-sharing and threat intelligence as the most effective international cooperation measures against cyber crime. (World Economic Forum)
- 63% of organisations do not have a process in place to assess the security of AI tools before they deploy them. (World Economic Forum)

- 72% of organisations have seen their cyber risks increase over the past 12 months. (World Economic Forum)
- 63% of businesses have also cited the ever-evolving and increasingly complex threat landscape as the greatest challenge in becoming cyber resilient. (World Economic Forum)
- 42% of American organisations are training their workforces to use AI tools compared to 32% globally. (Hays)
- 49% of organisations plan to increase security investments due to a breach, including incident response (IR) planning and testing, employee training, and threat detection and response tools. (IBM)
Statistics of Nature and Source of Cyber Threats
Cyber threats are manifold in nature, with attackers employing a variety of tactics to breach defences. Understanding the most common types of cyberattacks and the vulnerabilities they exploit is key to crafting an effective defence. The following stats depict the prevalent threat landscape.
- At 93% for businesses, phishing remains the most common type of cyber crime businesses experience, followed by hacking (8%), ransomware (7%), and denial of service (DoS) (5%). (GOV.UK)

- 97% of organisations have seen an increase in cyber threats since the start of the Russia-Ukraine war. (Accenture)
- 1% of users are responsible for 88% of data loss events. (Proofpoint)
- 68% of attacks originate via email. (Check Point)
- Stolen credentials account for 16% of initial infection intrusions, with email phishing attacks accounting for 14% and web comprise 9%. (Check Point)
- Plenty of emails are, unfortunately, making it past the filters. 56.5% of emails sent in 2023 were unsolicited spam emails. More than a third of all email messages are reported by survey respondents as spam. (OrbitMedia)
- Financial (17.4%), business and professional services (11.1%), high tech (10.6%), government (9.5%), and healthcare (9.3%) are attractive targets for both financially and espionage motivated actors. (Mandiant)

- 92% of organisations believe that their employees are well trained to spot phishing emails, yet many of these cyber incidents begin with staff opening suspicious links or files. (CrowdStrike)
- AI adoption is outpacing oversight. 97% of AI-related security breaches involved AI systems that lacked proper access controls. (IBM)
- 16% of breaches involve attackers using AI. These focus on human manipulation such as phishing (37%) or deepfake attacks (35%). (IBM)
- 50% of executives worry that large language models (LLMs) expose sensitive data, while 57% fear that threat actors could compromise AI model integrity through manipulated training data. (Accenture)
Statistics of Human Capital and Future Trends in Cyber Security
The human element plays a pivotal role in cyber security. Whether it's the shortage of skilled professionals, insider threats, or the future direction of cybersecurity roles, understanding the human capital dimension is vital. These statistics bring to light these aspects.
- 14% of businesses say they review the risks posed by their immediate supplier and 7% look to their wider supply chain. (GOV.UK)
- 86% of business leaders believe global political instability is likely to lead to a catastrophic cyber event in the next two years. (Accenture)
- 66% of AI leaders believe that AI will affect cybersecurity in the next 12 months but only 37% have processes in place for safe AI deployment. (World Economic Forum)
- 57% of organisations that turn to AI for security will have trained their cybersecurity workforce to use AI tools within the next year. (Hays)
- By 2027, 50% of large enterprise CISOs will have adopted human-centric security design practices to minimise cybersecurity-induced friction and maximise control adoption. (Gartner)
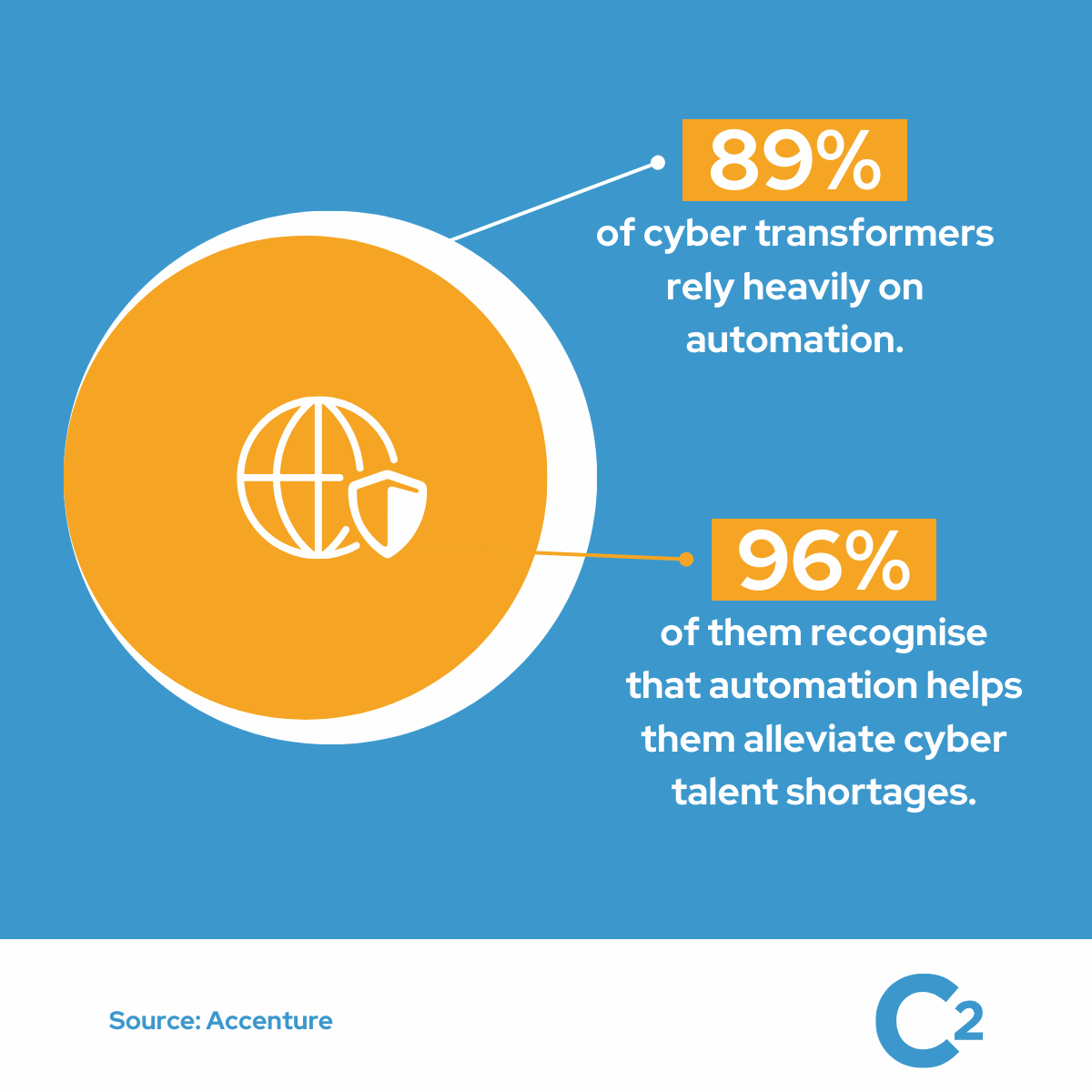
- 89% of cyber transformers rely heavily on automation. And 96% of respondents whose organisations substantially automate their cybersecurity programs recognise that automation helps them alleviate cyber talent shortages, a key challenge for any company seeking cyber resilience. (Accenture)
- 90% of leaders said the skills gap had affected their ability to implement their cyber security strategy. (Hays)
- The top five skills or implementations that would enhance security capability are cloud security, Governance, Risk, and Compliance (GRC), security architecture, security engineering, and Security Incident and Event Management (SIEM) or Security Operations Center (SOC). (Hays)
- Organisations that use security AI and automation saved an average of USD 1.9 million and shortened their breach times by 80 days. (IBM)
Protecting Your Business From Cyber Security Threats
Cybersecurity landscape is both dynamic and challenging, with ever-evolving threats and the relentless pursuit of solutions.
As we've observed from the cybersecurity statistics presented, the implications of cyber threats are profound, spanning from immediate financial losses to long-term strategic shifts. Businesses, irrespective of their size, are grappling with these challenges, making pivotal decisions on preparedness and strategic responses.
It's evident that while there is a growing awareness and investment in cybersecurity, there remains much to be done. Cybersecurity is not just a technical concern but a societal one, underpinning the safety and trust in our interconnected world.
A comprehensive risk management and business continuity management procedure will cover what is required to protect cyber security and business resilience. C2 Meridian's Risk Management module is an exceptional stand-alone RMS in its own right. However, when utilised as an integrated module to C2's BCMS, you unlock the power of the intelligent data stored within it.
By doing this, the system completely understands your organisational structure, exactly where everything is located, and knows the real-time impact if any part of your business, locations, systems, suppliers and more were to be disrupted. This means that the system can automatically assess the impact of any risk, and ensure the correct people within your organisation are notified of them without any added manual effort.
For a complete look at what C2 Meridian can do for your organisation, simply book a demo today.
Frequently Asked Questions about Cybersecurity (Cybersecurity FAQs)
1. Is it "cybersecurity" or "cyber security"?
The correct term is "cybersecurity." This compound noun refers to the practice of protecting systems, networks, and programs from digital attacks. The word is formed by combining "cyber," relating to technology and computers, with "security." While "cyber security" as two separate words can sometimes be seen in use, the widely accepted and most commonly used term in both professional and academic contexts is "cybersecurity."
2. Is there a difference between UK and US English in the use of the term "cybersecurity" or "cyber security"?
In both UK and US English, the term "cybersecurity" is generally used as a single, compound word. There's a common misconception that British English prefers "cyber security" as two separate words, while American English uses "cybersecurity." However, in practice, the single-word form "cybersecurity" is widely accepted and used in both language variants. It's important to note that language evolves, and variations can occur, but as of now, "cybersecurity" is the standard form in both UK and US English.
3. What is cybersecurity?
Cybersecurity refers to the practice and techniques used to protect computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks, unauthorised access, or damage. It encompasses a wide range of measures and technologies designed to safeguard digital assets and information from cyber threats. This includes implementing security policies, using antivirus software, securing network infrastructure, and educating users about safe computing practices.
4. Why is cybersecurity important?
Cybersecurity is crucial because it protects all categories of data from theft and damage. This includes sensitive data, personally identifiable information (PII), protected health information (PHI), intellectual property, data, and governmental and industry information systems. Without a cybersecurity program, an organisation or individual cannot defend themselves against data breach campaigns, making them an easy target for cybercriminals. The increasing volume and sophistication of cyber attackers and attack techniques compound the need for robust cybersecurity.
5. What are cybersecurity threats?
Cybersecurity threats are malicious acts that seek to damage data, steal data, or disrupt digital life in general. These threats include attacks like computer viruses, data breaches, Denial of Service (DoS) attacks, and other attack vectors. Cyber threats can originate from various sources, including corporate spies, hacktivists, terrorist groups, hostile nation-states, criminal organisations, lone hackers, and disgruntled employees. As technology evolves, so does the nature of these threats, making it essential to have updated and dynamic cybersecurity measures in place.
Written by Donna Maclellan
Lead Risk and Resilience Analyst at Continuity2
With a first-class honours degree in Risk Management from Glasgow Caledonian University, Donna has adopted a proactive approach to problem-solving to help safeguard clients' best interests for over 5 years. From identifying potential risks to implementing appropriate management measures, Donna ensures clients can recover and thrive in the face of challenges.


Written by Donna Maclellan
Lead Risk and Resilience Analyst at Continuity2
With a first-class honours degree in Risk Management from Glasgow Caledonian University, Donna has adopted a proactive approach to problem-solving to help safeguard clients' best interests for over 5 years. From identifying potential risks to implementing appropriate management measures, Donna ensures clients can recover and thrive in the face of challenges.